Search
0
2428
Biometric technology, which harnesses human characteristics such as fingerprints, facial recognition, and retinal scans for identification, has been steadily gaining traction in various sectors. The healthcare industry, always at the forefront of adopting technologies that improve patient care and operational efficiency, is no exception. Among the ..
0
2890
MIFARE® Cards: What Are They, Where Are They Used, and What Are the Different Types Available?In the realm of Radio-Frequency Identification (RFID) chips, MIFARE has grown into one of the most reputable and well-known brands around. Their technology has provided a trusted, innovative solution for RFID cards that works well across a number of diff..
0
9653
A Guide to Smart Card Readers: What Are They, How Do They Work and What Are the Different Types Available?
Smart card readers are becoming an increasingly common part of our digital lives, offering enhanced security, convenience, and a range of functionalities in our day-to-day lives. In this article, we will explore what smart card readers are, ho..
0
5394
Smart cards and associated accessories are a fascinating combination of cutting-edge technology and wearables. By combining the best of both worlds, they are quickly becoming an invaluable asset for organisations worldwide. Organisations must consider numerous factors when embracing this state-of-the-art technology, from smart cards to powerful ele..
0
2159
With the rise of technology, smart cards have become a vital tool in many industries. A smart card is an integrated circuit embedded into a card used for authentication and the secure storage of information.Smart cards are used in various industries where secure authentication and data storage are essential. In addition to providing digital securit..
0
7968
Teacher and student smart cards have become an increasingly popular tool in modern education systems. By providing universities, colleges, and schools with a way to better manage student enrollment, student/teacher data, attendance records, and student payment tracking, the student card revolution has seen great success across the educational lands..
0
1978
A student ID card is an essential part of student life, and a smart student ID card brings even more value and utility. Smart student ID cards provide a photo identification system that allows students to securely access university facilities, financial accounts, and services such as student discounts.Beyond the basic functions of a traditional stu..
0
17990
Is smart card cloning possible? The answer depends on what kind of smart card you're using and what it’s being used for.Over the last few decades, society has enjoyed a wealth of exciting and revolutionary technologies — technology that continues to evolve daily.However, consumers and businesses aren’t the only ones making good use of all that toda..
0
2747
In the 1950s if a criminal wanted to steal data or goods from your business they would break in, rummage around and make off with their swag.How things have changed!Now the ‘cyber criminal’ can be based anywhere in the world. Information is seen as the most valuable asset of a business and, this makes it liable to being targeted.Technology is at th..
0
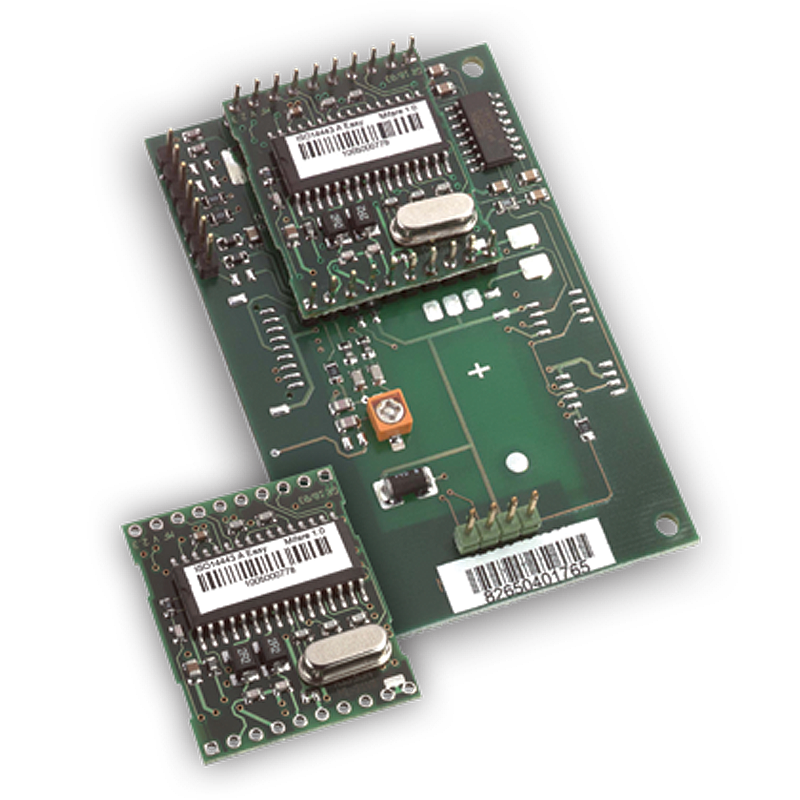
1050
OMNIKEY Embeddable Readers: The often forgotten part of the OMNIKEY familyOMNIKEY desktop readers are commonplace in many work environments and you may use them regularly. They’re a family of smart card readers that work with a wide range of card types and technologies. Technologies like; iCLASS Seos®, HID Prox®, iCLASS SE®, MIFARE®; and with some ..